Safeguarding Your Organisation's Sensitive Assets
In today's data-driven world, organisations face increasing challenges in managing and protecting their valuable data assets. The importance of data governance, with its focus on ensuring the availability, integrity, and confidentiality of data, cannot be overstated. Without proper data governance practices in place, organisations are at risk of data breaches, compliance violations, operational inefficiencies, and reputational damage.
Additionally, due to a number of recent high-profile data breaches affecting a significant number of Australians, a focus on the data being held and managed by many commercial organisations is coming under increased scrutiny by both the affected members of the public and by the relevant regulators and government agencies.
In this blog, we will delve into the topic of data governance and its profound impact on organisational security and success.
Firstly, we will define data governance and its significance in today's digital landscape. We'll explore how data governance goes beyond mere information security and touches upon every aspect of an organisation's data lifecycle. From data classification and access controls to privacy compliance and risk management, data governance sets the foundation for sound data management practices.
Next, we will highlight the potential risks and consequences organisations may face if they neglect or inadequately govern their sensitive data. We will paint a vivid picture of data breaches, unauthorised access, regulatory non-compliance, and the associated financial, legal, and reputational implications. Understanding these risks underscores the importance of implementing robust data governance measures.
Moreover, we will emphasise the symbiotic relationship between data governance and cybersecurity. These two disciplines work hand in hand to protect sensitive data from external threats and internal vulnerabilities. We will explore how data governance complements cybersecurity measures, such as access controls, data handling policies, incident response protocols, and security awareness training, to create a comprehensive defence against data breaches.
Finally, we will outline the essential steps required to establish a data governance capability within your organisation. From defining objectives, forming a dedicated team, assessing the current state, and developing a comprehensive data governance framework, we will provide a roadmap for effective implementation. We'll also emphasise the significance of stakeholder engagement, training, monitoring, and continuous improvement to sustain a successful data governance program.
Hopefully, by the end of this blog, you will have a solid understanding of the critical role data governance plays in safeguarding your organisation's sensitive assets and be equipped with insights and practical guidance to embark on your data governance journey.
Let's dive in and unlock the power of effective data governance for your organisation's security and success.
What is data governance?
Data governance refers to the overall management, control, and protection of an organisation's data assets. It encompasses the processes, policies, and frameworks that ensure data is accurate, consistent, secure, and accessible to authorised individuals. Data governance aims to establish a clear understanding of data ownership, accountability, and usage within an organisation, while also ensuring compliance with relevant regulations and industry standards.
A core part of a data governance program is understanding and managing the typical lifecycle stages of the information held by the organisation. Data lifecycle management is the process of managing data from its creation or acquisition to its retirement or disposal and includes the security of the data along the way.
The data lifecycle typically consists of the following phases:
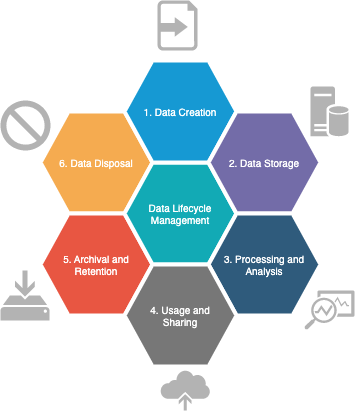 Data Creation: This phase involves the initial generation or acquisition of data. It can include activities such as data entry, data capture from external sources, or data generation through sensors or systems. During this stage, it is important to ensure that data is accurately and comprehensively captured.
Data Creation: This phase involves the initial generation or acquisition of data. It can include activities such as data entry, data capture from external sources, or data generation through sensors or systems. During this stage, it is important to ensure that data is accurately and comprehensively captured.- Data Storage: Once data is created, it needs to be stored in appropriate systems or repositories. This phase includes determining the storage infrastructure, such as databases, data warehouses, or cloud storage, and implementing data storage technologies that meet the organisation's requirements for accessibility, scalability, and security.
- Data Processing and Analysis: In this phase, data is processed, transformed, and analysed to derive insights, support decision-making, or generate reports. It involves activities such as data cleansing, data integration, data transformation, and data aggregation. Advanced analytics techniques, such as data mining, machine learning, or predictive modelling, may be applied to extract meaningful information from the data.
- Data Usage and Sharing: Once data has been processed and analysed, it is made available for use by authorised individuals or systems. This phase involves defining access controls, permissions, and data-sharing policies to ensure that data is accessed and used appropriately. Data may be shared across departments, teams, or external stakeholders based on predefined rules and agreements.
- Data Archival and Retention: Over time, certain data may become less frequently accessed or less relevant for immediate use. In this phase, data that is no longer actively needed is moved to archival storage. Archiving involves storing data in a cost-effective manner, often with reduced accessibility. Data retention policies are defined to determine how long data should be retained based on legal, regulatory, or business requirements.
- Data Disposal: At the end of its lifecycle, data may need to be disposed of securely. This phase involves implementing proper data destruction methods, such as data wiping, degaussing, or physical destruction, to ensure that data cannot be recovered or accessed by unauthorised individuals. Disposal processes should comply with applicable data protection regulations and organisational policies.
Throughout the data lifecycle, it is essential to apply data governance principles and practices to ensure data quality, security, and compliance. This includes maintaining data integrity, protecting sensitive data, documenting data lineage and metadata, and adhering to relevant regulations and privacy requirements.
By effectively managing the data lifecycle, organisations can optimise data usage, reduce storage costs, mitigate data risks, and ensure that data remains valuable and actionable throughout its lifespan.
What are the benefits of a Data Governance Program?
A broad data governance program is important for several reasons and provides a number of benefits including the following:
| Benefit | Description |
| Data Quality and Integrity | Effective data governance ensures that data is accurate, reliable, and consistent across systems and departments. It establishes standards for data entry, validation, and maintenance, reducing the risk of errors, duplication, and inconsistencies in data sets. |
| Regulatory Compliance | Data governance helps organisations meet legal and regulatory requirements related to data privacy, security, and confidentiality. By implementing policies and controls, organisations can ensure they adhere to data protection regulations such as the GDPR, HIPAA, or PCI DSS, avoiding legal repercussions and reputational damage. |
| Decision-making and Analytics | With proper data governance in place, organisations can have confidence in the quality and reliability of their data. This enables better-informed decision-making, as stakeholders can rely on accurate and consistent data for analysis, reporting, and strategic planning. |
| Data Security and Risk Management | Data governance includes establishing appropriate access controls, data classification, and encryption measures to protect sensitive information from unauthorised access, breaches, and misuse. It helps identify and mitigate risks associated with data handling, storage, and transmission. |
| Collaboration and Data Sharing | Data governance fosters collaboration and cooperation within organisations by providing a framework for data sharing and interoperability. It ensures that data is available to authorised individuals or departments, facilitating effective collaboration and knowledge sharing. |
| Cost Optimisation | Implementing data governance practices can lead to cost savings and operational efficiency. By reducing data duplication, improving data quality, and streamlining data management processes, organisations can minimise unnecessary expenses associated with data storage, maintenance, and data-related projects. |
| Stakeholder Trust and Reputation | Strong data governance practices enhance stakeholder trust, including customers, partners, and regulators. Demonstrating a commitment to data accuracy, privacy, and security helps build a reputation as a trustworthy organisation that values data integrity and respects privacy rights. |
Data governance plays a vital role in ensuring data quality, compliance, security, and reliable decision-making within organisations. It establishes a foundation for effective data management, mitigates risks, and promotes trust among stakeholders, ultimately driving business success in the data-driven digital landscape.
What Can Go Wrong If an Organisation Does Not Effectively Govern Its Sensitive Data?
Beyond the obvious impacts of data breaches and the associated damage to businesses, individuals, and governments, there are several other pitfalls that await the unprepared. Here are some of the major risks organisations face when they don't have their data governance game on point:
| Risk | Description |
| Data Breaches and Unauthorised Access | Without proper data governance measures, sensitive data becomes more vulnerable to breaches and unauthorised access. This can lead to financial losses, reputational damage, legal consequences, and compromised customer trust. Cybercriminals or internal bad actors may exploit security weaknesses and gain unauthorised access to sensitive information. |
| Data Inaccuracy and Inconsistency | Inadequate data governance can result in inaccurate, inconsistent, or incomplete data. This can lead to flawed decision-making, operational inefficiencies, and compromised business processes. Inaccurate data can also lead to compliance violations, as organisations may inadvertently base decisions or reporting on faulty information. |
| Regulatory Non-Compliance | Data governance helps organisations meet legal and regulatory requirements related to data privacy, security, and confidentiality. Without effective data governance, an organisation may fail to comply with these regulations, such as the GDPR, HIPAA, or industry-specific standards. Non-compliance can result in severe penalties, legal actions, and reputational damage. |
| Data Silos and Lack of Data Sharing | In the absence of data governance, data silos can emerge within an organisation. Departments or teams may independently manage and control their data, leading to fragmentation and hindered collaboration. This can impede insights, hinder efficient decision-making, and prevent the organisation from harnessing the full potential of its data assets. |
| Data Loss and Data Leakage | Inadequate data governance can increase the risk of data loss or leakage. Data may be accidentally deleted, corrupted, or misplaced, leading to irrecoverable losses. Additionally, without proper controls and monitoring, sensitive data may be shared or leaked, resulting in breaches, regulatory violations, and damage to an organisation's reputation. |
| Inefficient Data Management and Increased Costs | In the absence of effective data governance, organisations may struggle with inefficient data management practices. This can include data redundancy, poor data quality, and difficulties in data integration and retrieval. Inefficient data management processes can lead to increased operational costs, wasted resources, and hindered productivity. |
| Lack of Stakeholder Trust | When sensitive data is not effectively governed, stakeholders such as customers, partners, and employees may lose trust in the organisation's ability to protect their information. This can have detrimental effects on relationships, customer loyalty, and the organisation's reputation in the market. |
By implementing robust data governance practices, organisations can mitigate these risks, protect sensitive data, ensure compliance, and foster trust among stakeholders.
I’m specifically concerned about data breaches… How does a data governance program help prevent data breaches?
A data governance program can play a crucial role in assisting organisations to prevent data breaches by implementing policies, processes, and controls that help safeguard sensitive data.
Here's how a data governance program can provide mitigating controls and contribute to preventing data breaches:
| Control | Description |
| Data Classification and Inventory | Understand what data is being held! A data governance program establishes a process for classifying data based on its sensitivity and criticality. By identifying and categorising sensitive data, organisations can prioritise its protection and implement appropriate security measures. Creating a comprehensive inventory of data assets helps in understanding where sensitive data resides, who has access to it, and how it should be protected. |
| Access Control and User Permissions | Effective data governance ensures that access to sensitive data is limited to authorised individuals who need it for their job responsibilities. Access controls, such as role-based access control (RBAC) or attribute-based access control (ABAC), are implemented to enforce appropriate user permissions. This reduces the risk of unauthorised access and helps prevent data breaches caused by internal or external threats. |
| Data Handling Policies and Procedures | Data governance programs establish clear policies and procedures for handling sensitive data throughout its lifecycle. This includes guidelines for data collection, storage, usage, sharing, and disposal. By defining and enforcing these policies, organisations can ensure that employees understand their responsibilities and follow secure practices when working with sensitive data, reducing the likelihood of data breaches. |
| Data Security Controls | Data governance programs work in tandem with cybersecurity measures to implement technical controls for data security. These may include encryption, data masking, tokenisation, and secure transmission protocols to protect data at rest and in transit. Implementing strong security controls helps to mitigate the risk of unauthorised access or data breaches, even if other security measures fail. |
| Data Monitoring and Auditing | Data governance programs establish monitoring and auditing mechanisms to track data access, usage, and changes. By regularly monitoring data activities, organisations can detect suspicious behaviour, identify potential security incidents, and respond promptly to mitigate risks. Auditing also helps in identifying any gaps or weaknesses in the data governance framework, allowing for timely remediation. |
| Employee Training and Awareness | Data governance programs emphasise the importance of employee training and awareness regarding data security and privacy. By educating employees on best practices, data handling guidelines, and security protocols, organisations can foster a culture of security. Well-informed employees are more likely to understand the risks associated with data breaches and take necessary precautions to prevent them. |
| Incident Response and Data Breach Management | A data governance program should include an incident response plan to address data breaches promptly and effectively. This plan outlines the steps to be taken in case of a breach, including containment, notification, and recovery processes. By having a well-defined incident response plan in place, organisations can minimise the impact of a breach and prevent further data loss or compromise. |
A robust data governance program can go a long way to help prevent data breaches by implementing controls, policies, and procedures to protect sensitive data, manage access, monitor activities, and respond to security incidents effectively. By integrating data governance with cybersecurity practices, organisations can create a comprehensive framework for safeguarding their data assets and reducing the risk of data breaches.
What’s the relationship between data governance and cyber security?
Data governance and cybersecurity are closely interconnected and mutually reinforcing. Here's a brief breakdown of their relationship:
| Overlap | Description |
| Data Protection | Data governance and cybersecurity both aim to protect sensitive data from unauthorised access, breaches, and misuse. Data governance establishes policies, processes, and controls to ensure data privacy, confidentiality, and integrity. Cybersecurity measures, such as firewalls, encryption, and access controls, are implemented to enforce those policies and protect data from external threats. |
| Risk Management | Both data governance and cybersecurity play crucial roles in risk management. Data governance identifies and assesses data-related risks, such as data breaches or compliance violations, and establishes controls and mitigation strategies. Cybersecurity focuses on mitigating risks related to unauthorised access, malware, or other cyber threats. Working together, data governance and cybersecurity help organisations proactively identify and manage risks associated with data. |
| Compliance | Data governance is essential for meeting regulatory and legal requirements related to data privacy and protection. It ensures that data handling practices align with applicable regulations, such as the GDPR or HIPAA. Cybersecurity measures support data governance by implementing technical controls and safeguards that help organisations achieve and maintain compliance. |
| Incident Response | In the event of a data breach or security incident, data governance and cybersecurity collaborate to manage the response effectively. Data governance provides the framework for incident response plans, including protocols for containment, notification, and recovery. Cybersecurity teams, equipped with their expertise and tools, implement technical measures to address the breach and mitigate further damage. |
| Data Lifecycle Management | Data governance encompasses the entire lifecycle of data, including creation, storage, usage, and disposal. Cybersecurity measures are essential at each stage to protect data from unauthorised access or loss. For example, encryption and secure storage techniques are used to safeguard data at rest, while secure data transmission protocols protect data in transit. |
| Security Awareness and Training | Data governance initiatives promote security awareness and training programs for employees. These programs educate personnel on best practices for data protection, such as strong password management, recognising phishing attempts, and adhering to security policies. By integrating cybersecurity awareness into data governance, organisations can create a culture of security and enhance their overall defences. |
What data governance regulations or standards exist with a focus on Australia?
In Australia, there are several data governance regulations and standards that organisations need to consider. Here are some key ones:
- Privacy Act 1988: The Privacy Act regulates the handling of personal information by Australian government agencies and organisations covered by the Act. It sets out principles for the collection, use, disclosure, and security of personal data. Organisations are required to comply with the Australian Privacy Principles (APPs) and implement appropriate data governance practices to protect personal information.
Link: https://www.legislation.gov.au/Series/C2004A03712 - Notifiable Data Breaches (NDB) Scheme: The NDB scheme is part of the Privacy Act and requires organisations to notify affected individuals and the Office of the Australian Information Commissioner (OAIC) when a data breach is likely to result in serious harm. It emphasises the importance of having robust data governance measures in place to detect, respond to, and prevent data breaches.
Link: https://www.oaic.gov.au/privacy/notifiable-data-breaches/about-the-notifiable-data-breaches-scheme - Australian Information Security Manual (ISM): While the primary focus of the ISM is on information security, it encompasses various aspects of data governance as part of its overall objectives. The ISM includes specific controls and requirements related to data governance, such as data classification, access controls, data handling procedures, and incident response. These controls aim to ensure the proper management, protection, and privacy of data within government organisations.
Link: https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/ism - Australian Government Protective Security Policy Framework (PSPF): The PSPF provides a comprehensive framework for protecting Australian government resources, including information assets. It outlines principles and controls for managing and protecting sensitive government data, including data governance requirements, risk management, personnel security, physical security, and ICT security.
Link: https://www.protectivesecurity.gov.au/ - Australian Cyber Security Centre (ACSC) Essential Eight: The Essential Eight is a set of mitigation strategies developed by the ACSC to enhance cybersecurity resilience. While not specifically focused on data governance, it includes measures such as implementing application whitelisting, patching systems, restricting administrative privileges, and regular backups, which are integral to effective data governance practices.
Link: https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight - Australian Prudential Regulation Authority (APRA) Prudential Standards: APRA oversees the financial services industry in Australia and has specific prudential standards that include data governance requirements. For example, the Prudential Standard and Guidelines CPS/G 234 focuses on information security and CPG 235 on the management of data risk. These interrelated standards and guidelines require regulated entities to maintain an information security and data governance capability commensurate with the size and complexity of their operations.
Link: https://www.apra.gov.au/industries/1/standards - ISO/IEC 27001: While not specific to Australia, ISO/IEC 27001 is an international standard for information security management systems. Many organisations in Australia adopt this standard as a framework for implementing data governance practices related to information security, risk management, and compliance.
Link: https://www.iso.org/standard/27001
It's important for organisations to familiarise themselves with the regulations and standards applicable to their industry and ensure their data governance practices align with the requirements. Compliance with these regulations helps organisations protect sensitive data, maintain customer trust, and mitigate the risks associated with data breaches and non-compliance.
What are the typical steps required to establish a data governance capability for an organisation?
Establishing a data governance capability for an organisation involves a systematic approach and several key steps. The following provides a general outline of the typical stages needed to establish a data governance capability:
| Step | Description | |
| 1. | Define Objectives and Scope | Clearly define the objectives and scope of the data governance initiative. Determine what aspects of data governance you want to focus on, such as data quality, data privacy, or compliance. Identify the stakeholders involved and establish the overall goals and desired outcomes. |
| 2. | Form a Data Governance Team | Establish a dedicated team responsible for driving the data governance initiative. This team should include representatives from various departments or business units, including IT, legal, compliance, data management, and business users. The team will be responsible for developing and implementing the data governance framework. |
| 3. | Assess Current State | Conduct a thorough assessment of the organisation's current data landscape, including data sources, systems, processes, and governance practices. Identify any gaps, challenges, or areas of improvement in data management, data quality, security, and compliance. This assessment will help inform the development of the data governance framework. |
| 4. | Develop Data Governance Framework | Create or adopt a comprehensive data governance framework that outlines the policies, processes, roles, and responsibilities for managing data effectively. Define data governance principles, data standards, and guidelines for data classification, access controls, data quality, data lifecycle management, and data stewardship. Align the framework with industry best practices and relevant regulatory requirements. |
| 5. | Establish Data Governance Policies | Develop data governance policies that address data privacy, security, confidentiality, data sharing, and compliance. These policies should be aligned with relevant laws, regulations, and organisational requirements. Clearly define roles and responsibilities, including the data governance team, data stewards, data owners, and data custodians. |
| 6. | Engage Stakeholders and Gain Buy-in | Engage stakeholders across the organisation to gain their support and buy-in for the data governance initiative. Communicate the benefits and value of data governance, address any concerns, and encourage participation. Stakeholder involvement is crucial for the successful implementation and adoption of the data governance framework. |
| 7. | Implement Data Governance Processes | Implement the defined data governance processes and controls to manage data effectively. This includes establishing data quality management processes, data classification and labelling, access controls, data lifecycle management procedures, data privacy controls, and data audit and monitoring mechanisms. Integrate these processes into existing workflows and systems. |
| 8. | Provide Data Governance Training | Conduct training and awareness programs to educate employees about data governance principles, policies, and procedures. Ensure that employees understand their roles and responsibilities in data governance and are aware of data-related risks and best practices. Regularly reinforce data governance awareness to foster a culture of data stewardship and compliance. |
| 9. | Monitor, Evaluate, and Evolve | Continuously monitor and evaluate the effectiveness of the data governance program. Measure key performance indicators (KPIs) and metrics to assess the success and impact of data governance efforts. Identify areas for improvement, address challenges, and adapt the data governance framework as needed to meet evolving organisational needs and changing regulatory requirements. |
| 10. | Sustain and Embed | Embed data governance as an ongoing practice within the organisation. Establish governance mechanisms, such as data governance committees or steering groups, to oversee and guide data governance activities. Regularly review and update policies, processes, and controls to ensure they remain relevant and aligned with organisational goals and industry standards. |
Remember that each organisation's journey toward establishing a data governance capability may vary based on its unique requirements, industry, and size. It's essential to tailor the approach to suit your organisation's specific needs and leverage industry best practices to drive successful data governance implementation.
Conclusion
In an era where data breaches and privacy concerns dominate headlines, organisations must prioritise data governance as a foundational pillar of their information security and risk management strategies. Throughout this blog, we've explored the importance of data governance and its close relationship with cybersecurity.
Effective data governance serves as the guardian of sensitive data, providing the framework and processes to protect against unauthorised access, mitigate risks, ensure compliance with regulations, and promote responsible data management. It goes beyond mere technical controls and encompasses the holistic management of data throughout its lifecycle.
By establishing a robust data governance capability, organisations can proactively identify and address potential vulnerabilities, strengthen data protection measures, and foster a culture of data stewardship across all levels of the organisation. The integration of data governance with cybersecurity practices creates a formidable defence against data breaches, empowering organisations to protect their valuable assets and maintain customer trust.
The journey toward establishing a data governance capability requires careful planning, stakeholder engagement, and continuous improvement. By following the steps outlined in this blog, organisations can lay a solid foundation for effective data governance, tailored to their specific needs and compliance requirements.
As technology advances and data becomes even more critical to business operations, organisations must remain vigilant and adaptive. Remember, data governance is not just a checkbox to mark—it's a continuous journey that requires dedication, adaptability, and a commitment to data stewardship. With a strong data governance program in place, organisations can navigate the complex data landscape with confidence, harnessing the power of their data while mitigating risks and building trust among stakeholders.
So, take charge of your data. Establish a robust data governance capability and unlock the true potential of your organisation's most valuable asset. Your data deserves the best protection, and with effective data governance, you can thrive in a data-driven world.
Look out for more blog posts coming soon exploring the requirements and processes for developing and implementing Governance, Risk management and Compliance capabilities within your environment... And as always please reach out to us directly to discuss these topics further.

May 29, 2023