or... How to approach a complex GRC program!
As we discussed in the previous article (Governance, Risk and Compliance), to establish a robust cybersecurity program, organisations must prioritise effective governance, risk management, and compliance practices. These three elements work in tandem to help organisations identify and mitigate cybersecurity risks, adhere to regulatory requirements and industry standards, and align their cybersecurity objectives with their overall business goals.
While frameworks such as ISO27001 and PCI-DSS offer comprehensive guidance for implementing GRC practices in the cybersecurity domain, these frameworks can be large, complex and potentially overwhelming, particularly for organisations new to GRC.
However, we can simplify the process by focusing on fundamental GRC practices that are consistent across multiple frameworks. By establishing some foundational practices, organisations can approach GRC in a manageable and systematic way, regardless of the specific framework they choose to adopt.
Fundamental Questions to Consider.
To get started on the GRC journey it’s important to consider the following questions in the order presented below…
How do I know that the controls that I have implemented, effectively mitigate the risks identified for the assets that I need to protect?
Now I know that this seems a bit of a long-winded way to ask these questions, but stay with me, there is a point!
Building up in layers.
Most modern frameworks have moved to risk-based approaches that rely on these fundamental building blocks and questions. If we revisit the questions, we can start to see the artefacts and relationships that are common to most of these frameworks and should be driving the development and implementation of the GRC program.
What assets do I need to protect?
To determine what needs protection, you should conduct a comprehensive inventory of your organisation's assets, including data, hardware, software, facilities, and people. This inventory will help you identify the critical assets that are essential to your business operations and that require protection.
Key artefacts: Asset Management Policy/Standard and an Asset Register.
What do I need to protect my assets from?
Once you've identified your critical assets, you should assess the potential threats and risks to those assets. These threats could include cyber-attacks, natural disasters, theft, or other malicious activities. You should also consider the impact of those threats on your business operations and determine the likelihood and severity of each risk.
Key artefacts: Risk Management Policy/Standard and a Risk Register.
How do I protect my assets from the identified threats and risks?
To protect your assets, you should develop a risk management plan that outlines the controls you will implement to mitigate those risks. This plan should include administrative, physical, and technical controls that are tailored to your organisation's specific needs and risk profile. You should also prioritise the implementation of controls based on the risk level of each asset and controls should only be implemented if there is an associated risk.
Key artefacts: Risk Management Plan and a list of controls (if you are dealing with ISO27001 this is your Statement of Applicability or SoA).
How do I know that the controls that I have implemented, effectively mitigate the risks identified for the assets that I need to protect?
To ensure that your controls are effective, you should regularly review and assess your risk management plan. This review should include testing your controls to ensure they are functioning as intended and measuring the effectiveness of your controls in reducing your risk exposure. You should also monitor your environment for new threats and update your controls as necessary to address emerging risks.
Key artefacts: Metrics register and periodic report.
In Summary
This is the point I was alluding to above; you should now be able to see how these questions start to build up in related layers.
You have Assets that need to be protected.
Assets have Risks.
Assets have Risks that can be mitigated via Controls.
Assets have Risks that can be mitigated via Controls whose effectiveness is monitored via Metrics.
The idea here is to build up the necessary knowledge and structures to effectively manage your organisation's GRC program. This approach provides a systematic way of determining what needs to be done to protect your critical assets and helps you prioritise the implementation of controls based on the risk level of each asset. By following this approach, you can maintain traceability throughout the process and confidently answer difficult questions, such as "Why are we investing significant resources in implementing control x?"
As an example, the diagram below highlights in red how this approach aligns with the ISO27001 framework.
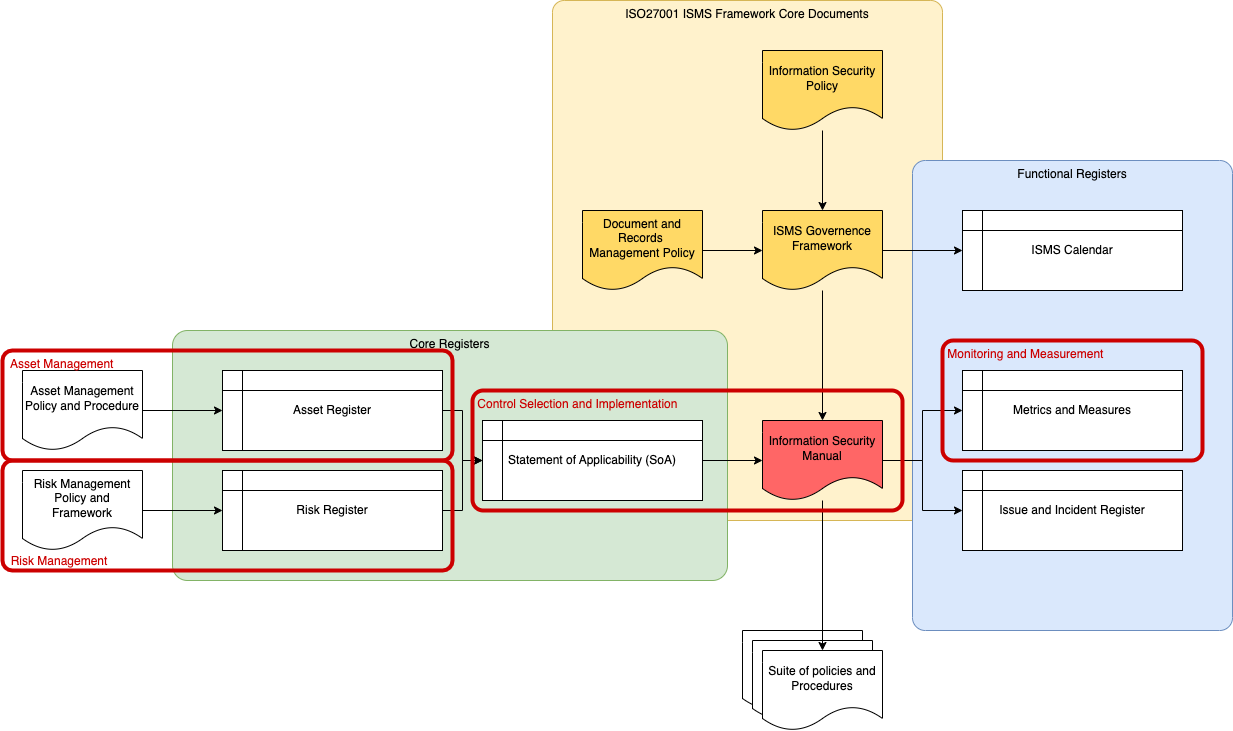 Final notes
Final notes
By establishing the core artefacts for asset management, risk management, and control implementation, organisations can effectively protect their critical assets from threats and start the processes needed to meet regulatory and compliance requirements.
If you have these structures in place you will be well-placed to approach just about any modern GRC program, and while implementing a GRC program may seem like a daunting task, by focusing on the fundamental practices outlined above, organisations can simplify the process and approach it in a manageable and systematic way.
Even if you are not looking to go for formal certification against one of the many GRC frameworks out there, establishing the core knowledge and fundamental practices outlined above will go a long way in ensuring that you can protect your business and clients from attacks and other adverse events.
We encourage readers to learn more about GRC in cybersecurity and how to implement effective GRC strategies in their organisations. This will help them establish a strong cybersecurity program that protects their organisation from cyber threats and builds a culture of cybersecurity awareness and accountability throughout the organisation.
Look out for more blog posts coming soon exploring the requirements and processes for developing and implementing Governance, Risk management and Compliance capabilities within your environment... And as always please reach out to us directly to discuss these topics further.

May 1, 2023