GOVERNANCE, RISK AND COMPLIANCE
Contact a GRC Expert
Achieve excellence in GRC implementation today. Contact us to assess, design, implement, and operate robust GRC frameworks. Safeguard your organisation with our support across industry-leading frameworks such as ISO27001/2, NIST, Essential 8/ISM/IRAP, APRA CPS-234, SOC2, PCI-DSS, AESCSF, and more.
Don't compromise on security and compliance! Partner with us for tailored solutions. Reach out now to start your GRC journey towards long-term success.
Our Approach
Our GRC services are designed to help organisations ensure that they are operating in compliance with relevant laws and regulations, as well as internal policies and procedures. This includes identifying and managing risks, establishing effective governance structures, and implementing appropriate controls to mitigate those risks. A comprehensive GRC implementation supports organisations to achieve their goals by ensuring that they are operating in a responsible and compliant manner, while also managing the risks that could impact their success.
GRC programs across multiple frameworks should be approached in a phased and cyclic manner to ensure ongoing relevance and continuous improvement. The approach to a typical GRC engagement can be broken down into the phases below.
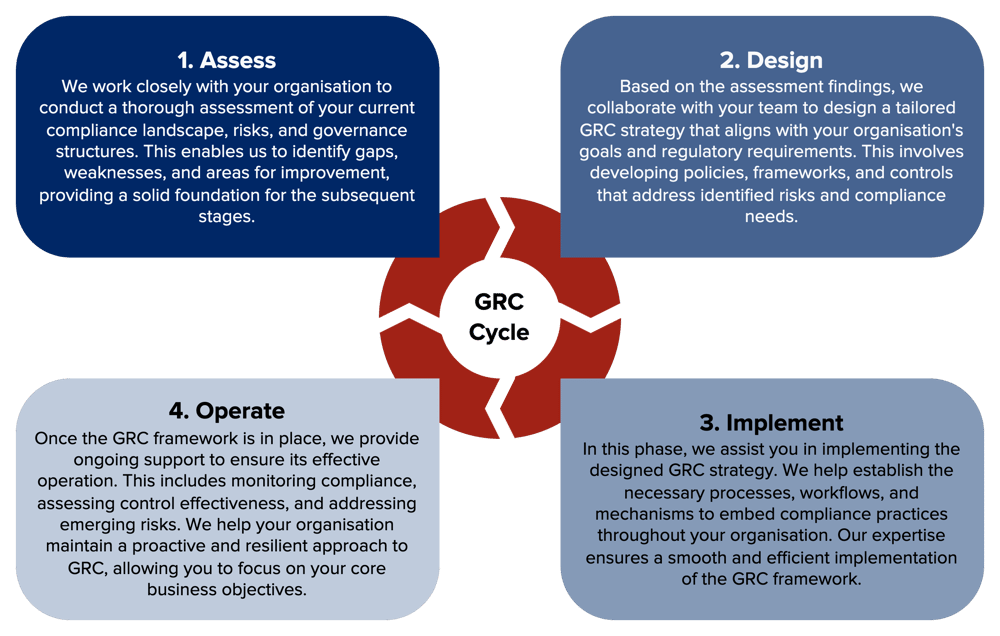
Approaching GRC engagements in this systematic manner can provide significant benefits. It ensures a proactive approach to compliance and risk management, reducing the likelihood of regulatory violations, financial losses, and reputational damage. By integrating GRC principles into your operations, you can confidently pursue your goals, knowing that you have robust processes in place to protect your interests.
Supported Frameworks
At ITSEC we have extensive experience supporting many common GRC frameworks. While the list below highlights some of the frameworks we support, it is by no means exhaustive. We understand that different organisations may have unique requirements, and we are well-equipped to adapt our services to custom or regional frameworks as needed.
We encourage you to reach out to us so that we can discuss your requirements and provide tailored solutions to address your unique GRC challenges.
ESSENTIAL 8
In response to the increasing prevalence of cyberattacks, the Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) recently developed a set of strategies to help organisations mitigate common attack vectors. These strategies are known as the Essential Eight. The Essential Eight is divided into three main objectives, which are then further divided into eight strategies. If your organization finds itself in the category of maturity level one or two, then ITSEC can certainly help you mature your cybersecurity to the point where you can achieve a level three maturity in your cybersecurity posture.
ISM & IRAP
The Australian Government Information Security Manual (ISM) is a comprehensive guide that provides cybersecurity guidance for Australian government agencies. It is published by the Australian Cyber Security Centre (ACSC) and serves as a framework to protect government information and systems from cyber threats.
The ISM outlines a range of security controls and practices that government agencies should implement to ensure the confidentiality, integrity, and availability of sensitive information. It covers various areas such as risk management, personnel security, physical security, network security, and incident response.
The Information Security Registered Assessors Program (IRAP) is an initiative by the Australian Signals Directorate (ASD) to provide independent security assessment services. The program aims to help government agencies and organisations assess and certify the security of their information and communication technology (ICT) systems against the requirements specified in the ISM.
By participating in the IRAP program and obtaining certification, organisations demonstrate their commitment to implementing robust cybersecurity practices and protecting sensitive information. It helps build trust among government agencies and other stakeholders, as well as enhances the overall cybersecurity posture of the organization.
Both the ISM and the IRAP program play crucial roles in strengthening cybersecurity within the Australian government and supporting the protection of sensitive information and critical infrastructure from cyber threats.
ISO 27001 / ISO 27002
ISO 27001 is a popular & well-accepted security standard & certification to implement & showcase an organization’s security posture. The objective of the standard is to “provide requirements for establishing, implementing, maintaining and continuously improving an Information Security Management System (ISMS)”. The independent certification to the standard is recognised around the world as an indication that your organisation is aligned with information security best practices.
APRA CPS-234
APRA CPS 234 is a prudential standard established by the Australian Prudential Regulation Authority (APRA) that focuses on information security for regulated entities in the financial services industry. It sets out requirements for organizations to protect their information assets from cyber threats, including establishing a robust information security framework, implementing appropriate controls, and ensuring effective incident management and response. CPS 234 aims to enhance the resilience and security of critical information assets and promote the stability of the financial system by mitigating the risks associated with cyber-attacks and data breaches.
NIST CSF
NIST Cybersecurity Framework is a voluntary framework that consists of customisable standards, guidelines, and best practices to manage cybersecurity-related risk. The main purpose of NIST CSF is “Improving Critical Infrastructure Cybersecurity,” The Cybersecurity Framework’s prioritised, flexible and cost-effective approach helps promote the protection and resilience of critical infrastructure.
AESCSF
In recent years, the security and reliability of the Australian energy sector has fallen under increasing attention due to sophisticated cyber‐attacks against critical infrastructure in several global jurisdictions. The consequence of these attacks in Australia may not only impact energy organisations, but have broader impacts on society, public health and safety, and our nation’s economy.
The Australian Energy Sector Cyber Security Framework or AESCSF is a cyber security framework that has been developed and tailored to the Australian energy sector. The Framework aims to enable Participants to assess, evaluate, prioritise, and improve their cyber security capability and maturity. The Framework provides a standardised approach for Participants to evaluate their cyber security capability and maturity and empowers Participants to make informed decisions regarding the steps they need to take to become resilient in the face of a cyber‐attack.
PCI-DSS
PCI DSS (Payment Card Industry Data Security Standard) is an information security standard for organisations that handle and process credit card transactions. It is presided over by all the major credit card providers including American Express, Visa, Mastercard, Discover, and JCB. Like the healthcare industry, the payment card industry retains and processes billions of sensitive records annually, making organisational security paramount. PCIDSS ensures that controls are in place to limit access to cardholder data, protect the confidentiality of transactions, and continuously protect organisations’ security posture through mandatory testing and scanning by certified PCI ASV testers.
GDPR
A breach of the GDPR requirements can results in fines and mandates that can significantly impact your ability to operate your business and additional fines, compliance mandate, etc. If your business is collecting and/or storing data from citizens or residents in Europe, you will be affected by the provisions of GDPR. Complying to GDPR takes more than adding a banner to your website making visitors aware of cookies from your website. European citizens have a right to request their personal data in an easily readable format that provides the relevant information on the data being processed, the purpose, and if it was sent to a third party.
HIPPA & HITRUST
The Health Insurance Portability and Accountability Act (HIPAA) passed by the US House of Representatives defines how electronic protected health information (ePHI) needs to be managed and secured. Whether you are a Covered Entity (CE) or a Business Associate (BA) there are policies, procedures and processes you need to comply with. As data breaches and regulatory oversight increases on health-related companies, maintaining HIPAA compliance is the absolute minimum standard companies should adhere to.
Health Information Trust Alliance (HITRUST) CSF is a certifiable framework, designed to provide organisations who work with health data with a comprehensive & streamlined approach to regulatory compliance, privacy & risk management. Thus, the HITRUST CSF supports HIPPA and aids in safeguarding electronic protected health information (ePHI) & other critical information and helps organisations streamline their security and compliance requirements.
SOC2
A SOC 2, or “System and Organisation Controls 2” is quickly becoming one of the most sought-after compliance standards in North America. The SOC 2 framework is an auditing procedure that ensures your service providers securely manage the data to protect the interests of your organization and client’s privacy on five principles – Security, Availability, Processing integrity, Confidentiality and Privacy.
Discover The Power of Comprehensive GRC
Discover the power of comprehensive Governance, Risk and Compliance (GRC) services and safeguard your organisation's success. Our expert team is dedicated to assisting you in navigating the complex landscape of laws, regulations, and internal policies. Take the first step towards a responsible and compliant operation with our tailored GRC services and partner with our specialists for comprehensive GRC services that safeguard your organisation's compliance, mitigate risks, and propel your success.
Contact us today to discuss your specific needs and embark on a journey towards a secure and compliant future.
Book in below at a time that suits you to discuss your specific requirements or challenges!
Let's talk cyber security.
Get in touch and schedule a call with our experts and we'd love to help you with your cyber security needs.